Let’s start by asking a simple question before we get into cybersecurity. Would you be comfortable working with a forklift operator who has not received proper training?
We hope your answer is “NO”. Unless your employees know what they are doing, they could cause a lot of damage to your business. That would be a huge potential business risk.
The next question is: how much damage can a person without training do to your corporate network?
In the end, there is a lot to say.
Ransomware is typically distributed through phishing emails. Employees are tricked into clicking malicious links and/or installing malicious software, compromising the company’s network.
Attackers use social engineering to manipulate their victims into doing something they really shouldn’t do. They often pretend to be an executive or business partner by using specific information.
What sources do they use to gather this information?
Would an attacker gain that much insight into your company and employees that they can target you in such a way? How do they do that? Do they scour the Dark Web or mine databases?
Not likely. The public is already privy to so much juicy information, so why go through all that trouble?
Look at the website of your company. Imagine what an attacker might learn from your website and how they might use that information to send you a phishing email.
Are you still unsure? Here’s a trick. Type these words into your Google search:
filetype: pdf site:nswits.au
In this case, “nswits.ca” is your company’s domain name.
The PDF documents hosted on your site, some of which shouldn’t be made public, will be listed here.
Developing an example to demonstrate what information could be harvested while writing this blog post. One common target of threats is hospitals.
We found a Privacy Awareness Training sample (redacted image below) that includes complete contact information for the Chief of Staff. A phishing email tells an attacker who to contact and what should be included.
As a result, attackers can quickly gather the required surveillance to launch an attack by exploiting over-sharing on a website.
Do You Know What to Do?
Your website can be extended to high security by controlling how much information it shares. On the other hand, there will always be information you need to share or share by your partners/vendors or your employees via social media and competitive intelligence sites.
You cannot control how much information is shared about your company; however, it is possible to maintain your employees’ resilience to these attacks. A robust cybersecurity awareness training program is the solution to this problem.
NSWITS Cybersecurity Awareness Training is one of many solutions available on the market. Although they have a free version, the true power of this training is unlocked once the premium version is purchased, as it allows simulated phishing emails to be sent to test how well employees deal with threats.
How is this made possible?
Training in cybersecurity awareness isn’t too complicated on the technical front. Some IT expertise is needed to set up the online portal, configure the email settings, and manage the learning materials.
In addition, the price is reasonable at about $35/user/year so that you won’t break the bank.
Employees can be trained in small increments over 90 minutes, so training is not too intrusive.
As such, this is a low-effort, low-cost security measure of high impact.
In most cases, cyberattacks on your company are the fault of third parties. These nefarious programmers write malware to steal your company’s intellectual property, steal your customers’ confidential information, or exploit your financial information.
Cybercriminals may even come from within through employees’ ignorance and negligence.
You will find tips in this blog about educating your employees about cybersecurity. Preventing data breaches starts with training employees. React quickly. Develop policies for securing your business based on the assumption that attacks will occur, then teach employees what they should do (and not do) to do so.
1. Cybersecurity Should Be A Top Priority In Workplaces.
Cyber incidents may impact your organization’s operations and the responsibilities of employees, particularly about mobile devices, should be explained.
The requirement to read and understand the company IT policies and sign an “I have read and understood this policy” is not enough.
External Threats Visible
B2B International conducted a survey recently in which 94% of companies reported external threats.
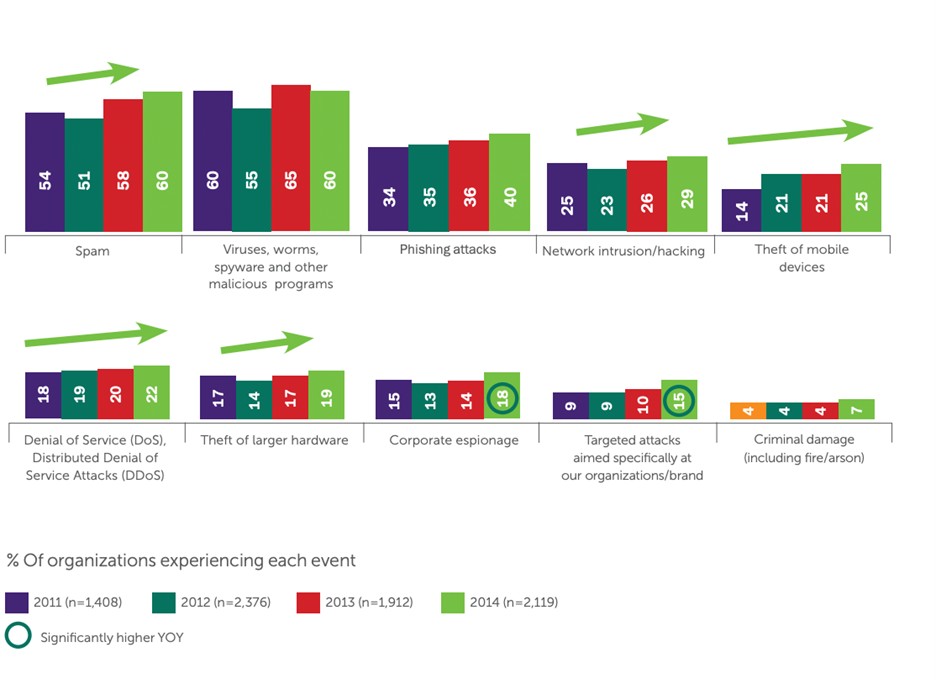

Credit: A report on security threats and data breaches by B2B International, October 2014.
2. It Officers And Top Management Are Equally Employees
Top managers are often targeted because:
More information is available to them. Bad guys recently targeted Travelling executives using free hotel Wi-Fi without encryption.
— The IT department bends the rules for them.
— The financial impact/damage can be more significant.
IT professionals are also vulnerable because they have access to the network on an unlimited basis.
3. Advise Your Employees That, While You Make The Best Efforts To Secure The Infrastructure Of The Company, Any System Is Only As Secure As Its Weakest Link.
- Promote collaboration, not just compliance.
- Develop a comprehensive policy that covers all attack vectors.
- Accept that humans make mistakes and have weaknesses.
4. Engage Employees In Regular, Directed Conversations About Cyber Attacks.
- You should include cybersecurity training in your general onboarding process since new employees are always starting work.
- Participate in various formats (e.g., Lunch and Learn).
Put it to good use. — Many employees have PCs at home, as well as relatives who need support.
Valuable content should be provided. Refer to current news stories. Utilize social media.
5. Survey Social Engineering Activities Carefully.
- When using corporate devices or social media, be careful of links from social media, blogs, and suspicious sources.
- Cybercrime often begins with someone pretending to be a co-worker, asking seemingly innocuous questions about the company and its operations.
- Cybercriminals who take advantage of social weaknesses rarely look like them
6. Inform Employees How To Detect An Attack.
Put policies in place, assuming you will be hacked. React immediately. Maintain an updated or reviewed remediation plan regularly.
- Communicate precisely what employees should do if they think they have witnessed a cyber incident.
It is important to train before there is a problem. It is essential for training to include specific rules for email, browsing the Web, using mobile devices, and interacting with social media.
Keep the basics in mind:
- Disconnect your computer physically from the network.
- Contact your administrator if you receive any suspicious emails or notice any unusual activity on your mobile device.
- Start memorizing your emergency IT number if you can’t find it in 20 seconds or less!
7. Never Disapprove Or Impose A Reaction To A Red Flag By An Employee.
- Even if a false alarm is raised, employees shouldn’t be discouraged from reporting actual cyberattacks.
- Improve your training approach if false alarms occur frequently.
8. Be As Prompt As Possible With A Heads-up If An Incident Occurs.
- If a cyber incident is not appropriately handled or transparently, its impact can significantly increase.
- Communicate instructions on how to address the public and the media.
- Make sure to have a solid internal communications plan and public relations strategy in place before any significant events.
- Ensure your computer is against cyber-attacks.
9. Evaluate The Cybersecurity Knowledge Of All Employees Regularly.
- Ensure it is relevant to their digital lives.
- Provide incentives for prompt responses (or make it fun and rewarding).
10. Feedback Is Invited, Listened To And Responded To.
- If you require your employees to change passwords every week, be prepared for them to write them down and post them on their desktops.
- They will use fewer specific workarounds such as personal email and USB sticks to get around restrictions if access to the information they need is too complicated.
Identify unsafe behaviors’ root cause.
The result will be your employees learning from their mistakes if you run regular (practice) attacks. You’ll also find out where improvements are needed in your organization so that you can plan future training sessions appropriately. An effective practice attack teaches us why security is vital by not falling for the same trick twice.
Conclusion
Business owners must take precautions against data breaches and hacks as these incidents rise. The same is true for any organizational transformation project: you must get your team on board and build habits.
A combination of training and constant reminders that threats exist may also be effective, as well as a “live fire” exercise that illustrates how easily you get attacked. It’s essential to put your team in a position to succeed in cybersecurity.







